AI has transformed how organizations detect and respond to anomalies in their systems and operations. By using advanced algorithms like isolation forests, one-class SVMs, autoencoders, and neural networks, AI-powered anomaly detection solutions can:
- Identify unknown issues that traditional methods miss
- Reduce false positives and false negatives
- Enable real-time response to emerging threats and anomalies
As data volumes grow and threats become more complex, AI offers a proactive approach to stay ahead of potential breaches, process inefficiencies, and equipment failures across industries like cybersecurity, finance, healthcare, manufacturing, and IT infrastructure.
| Key Benefits | Traditional Methods | AI-Powered Solutions |
|---|---|---|
| Handling Large Data Volumes | Struggle | Can process huge datasets |
| Handling Unstructured Data | Limited to structured data | Handle any data format |
| Adapting to New Threats | Miss evolving threats | Adapt to new patterns |
| Accuracy | High false positive/negative rates | More accurate results |
| Detection Speed | Slow detection | Real-time anomaly spotting |
While AI anomaly detection offers significant advantages, it also presents challenges around data quality, computational resources, model interpretability, and ethical considerations like bias mitigation.
Related video from YouTube
Problems with traditional methods
Large data volumes
Old methods can't handle big data sets well. As more data comes in, these methods get slower and can't find unusual patterns quickly enough.
Complex, unstructured data
Data comes in many formats these days - social media posts, sensor readings, and more. Traditional methods were made for structured data and struggle with this variety, leading to mistakes.
Evolving patterns and threats
Threats and unusual patterns keep changing. Methods that rely on fixed rules can't adapt, missing new threats and giving false alarms.
False positives and negatives
Too many false alarms and missed threats are common with old methods. This wastes time and resources while leaving real issues undetected.
Real-time detection and response
Traditional approaches are often too slow for real-time threat detection and response. Delays in finding issues can lead to serious problems like data breaches or system failures.
These weaknesses show why we need better anomaly detection using AI and machine learning:
| Traditional Methods | AI/Machine Learning |
|---|---|
| Struggle with big data | Can process huge datasets |
| Limited to structured data | Handle any data format |
| Miss evolving threats | Adapt to new patterns |
| High false positive/negative rates | More accurate results |
| Slow detection | Real-time anomaly spotting |
AI for Anomaly Detection
Supervised Learning
Supervised learning trains AI models to identify normal and unusual patterns using labeled data. This approach works well when you have enough labeled data available. The benefits:
- High accuracy
- Can detect known anomalies
However, it requires a lot of labeled data, which can be time-consuming and costly to obtain. Supervised models may also struggle with unknown or new anomalies.
Unsupervised Learning
Unsupervised learning algorithms can find anomalies in unlabeled data without prior training. This is useful when you have little or no labeled data. These algorithms identify patterns and relationships that may indicate anomalies. The benefits:
- Can detect unknown anomalies
- No need for labeled data
However, unsupervised models may not be as accurate as supervised ones. They may also require extra processing to identify the anomalies.
Semi-Supervised Learning
Semi-supervised learning combines supervised and unsupervised techniques. It uses a small amount of labeled data to train the model, then applies unsupervised algorithms to find anomalies in unlabeled data. This approach balances the accuracy of supervised learning with the flexibility of unsupervised learning.
Deep Learning
Deep learning models, like neural networks, can effectively find complex patterns and anomalies in data. They are particularly useful for high-dimensional data, such as images and sensor readings. The benefits:
- High accuracy
- Can detect complex patterns
However, deep learning models require large amounts of data and computing power, which can be challenging.
| Learning Approach | Pros | Cons |
|---|---|---|
| Supervised | - High accuracy - Detects known anomalies |
- Requires a lot of labeled data - May miss unknown anomalies |
| Unsupervised | - No labeled data needed - Finds unknown anomalies |
- May be less accurate - Extra processing needed |
| Semi-Supervised | - Balances accuracy and flexibility | - Still needs some labeled data |
| Deep Learning | - Highly accurate - Handles complex patterns |
- Needs large datasets - Computationally intensive |
AI algorithms for anomaly detection
AI algorithms are key for finding unusual data points or "anomalies." Here are some common AI methods used:
Isolation Forest
This method uses many decision trees to isolate data points far from the average. It's good at spotting outliers.
One-Class Support Vector Machines (OC-SVM)
OC-SVM is a type of machine learning model. It learns from normal data to create a boundary separating normal from anomalous data.
Autoencoders
Autoencoders are neural networks that compress and recreate data. They can identify anomalies by failing to recreate certain data points accurately.
Variational Autoencoders (VAE)
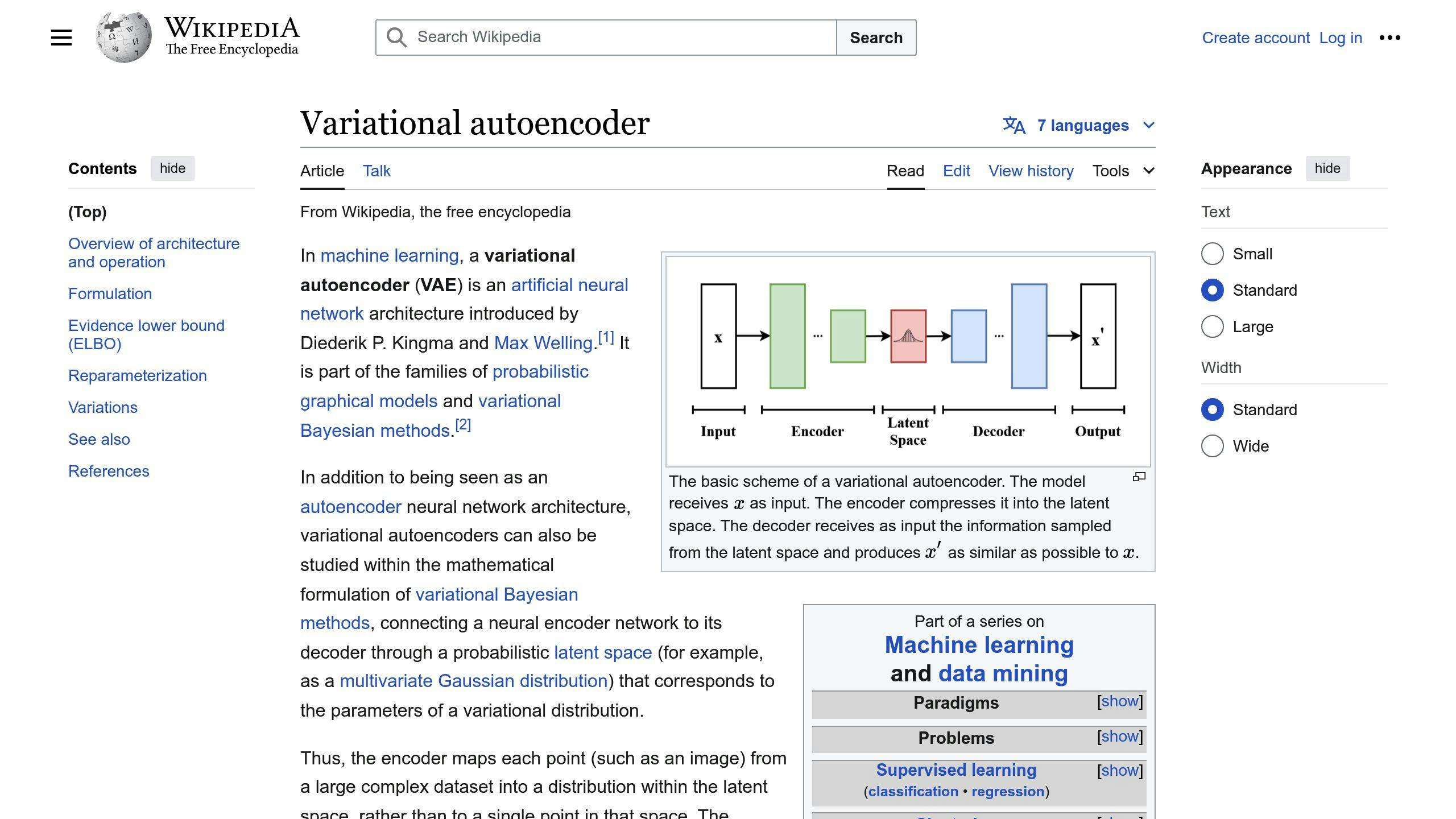
VAEs are a type of autoencoder using probability to compress data. They spot anomalies by giving low probability to certain data points.
Generative Adversarial Networks (GANs)
GANs have two neural networks working together to generate new data like the training data. They detect anomalies by failing to generate certain data points.
Recurrent Neural Networks (RNNs)
RNNs are neural networks designed for sequential data like time-series. They can find patterns and outliers in this type of data.
These AI algorithms help detect anomalies in areas like cybersecurity, healthcare, finance, and industrial systems.
| Algorithm | How it Works |
|---|---|
| Isolation Forest | Uses many decision trees to isolate outliers |
| One-Class SVM | Learns normal data to create a boundary separating anomalies |
| Autoencoders | Fails to recreate anomalous data accurately |
| Variational Autoencoders | Gives low probability to anomalous data |
| Generative Adversarial Networks | Fails to generate anomalous data |
| Recurrent Neural Networks | Finds patterns and outliers in sequential data |
sbb-itb-9890dba
Applications of AI Anomaly Detection
AI-powered anomaly detection has many uses across different industries. It helps organizations find unusual patterns, spot threats, and improve operations.
Cybersecurity and Fraud Prevention
In cybersecurity, AI detects malicious activities like hacking attempts or unauthorized access. By analyzing network traffic, user behavior, and system logs, AI models can identify anomalies that signal cyber threats. This allows organizations to respond quickly to potential security breaches and prevent financial losses.
AI also helps detect fraudulent transactions or insurance claims by finding unusual patterns in financial data.
Industrial Monitoring and Maintenance
In industrial settings, AI analyzes sensor data to detect anomalies that indicate equipment failures or inefficiencies. This enables proactive maintenance, reducing downtime and extending the lifespan of critical assets.
For example, AI can detect unusual vibrations in machinery, predicting potential failures and allowing for timely repairs.
Healthcare Monitoring
In healthcare, AI monitors patient health data and medical imaging to identify potential medical issues. By analyzing electronic health records, scans, and sensor data, AI models can detect anomalies that indicate chronic diseases like diabetes or heart disease. This enables early interventions and improves patient outcomes.
Financial Risk Management
In finance, AI monitors transactions to detect and prevent fraudulent activities. By analyzing transaction data, AI models can identify unusual patterns, such as sudden changes in spending habits or location-based anomalies. This allows organizations to respond promptly to potential fraud and minimize financial losses.
Network and System Monitoring
In IT infrastructure, AI detects security threats and optimizes system operations by monitoring network performance. By analyzing system logs, network traffic, and performance metrics, AI models can identify anomalies that indicate performance issues, security breaches, or system failures. This enables organizations to respond promptly and minimize downtime.
These applications show how AI anomaly detection can help various industries detect and respond to anomalies in real-time, improve efficiency, and reduce risks.
| Industry | Use Cases |
|---|---|
| Cybersecurity | Detect malicious activities, unauthorized access |
| Industrial | Predict equipment failures, optimize processes |
| Healthcare | Monitor patient data, identify medical issues |
| Finance | Detect fraudulent transactions, spending anomalies |
| IT Infrastructure | Monitor network performance, security threats |
Challenges and Considerations
Data Quality and Availability
AI models need high-quality data to learn properly. However, issues like noise, missing values, duplicates, and imbalances can impact model performance. Having enough relevant, diverse data is crucial for accurate anomaly detection.
Computational Resources and Scalability
AI models can be resource-intensive, requiring significant computing power to process large datasets. As data volumes grow, scalability becomes a challenge. Organizations must ensure they have the infrastructure to support AI-powered anomaly detection.
Model Interpretability and Explainability
As AI models become more complex, it can be difficult to understand how they arrive at their conclusions. This lack of transparency can lead to mistrust and difficulty identifying errors. Developing interpretable and explainable AI models is vital for building trust and accountability.
Ethical Considerations and Bias Mitigation
AI models can perpetuate biases present in the data, leading to unfair outcomes. Organizations must address these biases and implement measures to mitigate them, such as using diverse datasets, regular auditing, and implementing fairness metrics.
| Challenge | Description |
|---|---|
| Data Quality and Availability | Ensuring high-quality, relevant, and diverse data for effective model learning. |
| Computational Resources and Scalability | Having the necessary infrastructure and resources to support AI-powered anomaly detection as data volumes grow. |
| Model Interpretability and Explainability | Developing transparent and understandable AI models to build trust and identify errors. |
| Ethical Considerations and Bias Mitigation | Addressing biases in data and implementing measures to ensure fair and unbiased outcomes. |
Conclusion
AI has transformed how organizations detect and respond to irregularities in their systems and operations. By using advanced algorithms and machine learning, AI-powered anomaly detection solutions can:
- Identify unknown issues
- Reduce false positives and negatives
- Enable real-time response to emerging threats
As data volumes grow and threats become more complex, traditional anomaly detection methods are no longer sufficient. AI offers a proactive approach, allowing organizations to stay ahead of potential breaches and protect their systems.
The future of AI-powered anomaly detection looks promising. Emerging trends like explainable AI, blockchain, and edge computing are expected to further improve accuracy and efficiency. As technology evolves, we can expect more innovative applications of AI in anomaly detection, from predictive maintenance to medical diagnosis.
| Traditional Methods | AI-Powered Solutions |
|---|---|
| Struggle with large data volumes | Can process huge datasets |
| Limited to structured data | Handle any data format |
| Miss evolving threats | Adapt to new patterns |
| High false positive/negative rates | More accurate results |
| Slow detection | Real-time anomaly spotting |
FAQs
How can AI help identify abnormal user behavior within a network?
Behavioral Analysis
AI systems can analyze network behaviors over time to detect subtle changes or trends that may indicate emerging threats or sophisticated cyber attacks. These systems learn from historical data and real-time observations to identify previously unseen attack patterns.
What are the applications of anomaly detection?
Anomaly detection has various applications, including:
| Application | Description |
|---|---|
| Fraud Detection | Spotting fraudulent financial transactions |
| Manufacturing | Detecting faults or defects in products |
| Cybersecurity | Identifying unauthorized access or intrusions in computer networks |
| Aviation | Monitoring sensor readings for potential issues in aircraft |
| Healthcare | Detecting potential risks or medical problems in patient data |
| Predictive Maintenance | Identifying equipment or system failures before they occur |